
– By Hardik Bansal
– Intern IPPCS’21
INTRODUCTION
When we talk about cyberspace of any country it highlights one particular grey area in the field of law wherein the legal issues as well as various aspects are still something that have not been developed to a great extent. However, at a very basic fundamental understanding we can be certain of one thing; that regardless of whatever we argue a sovereign country exercises full control over its territory, as held in the Case of SS Lotus by the International Court of Justice and in extension the principle of territorial sovereignty applies to cyberspace as well and it protects the cyber infrastructure located within a state’s territory. Despite clarity on this aspect cyber crimes are on a rise and there are not many legal instruments especially when we talk about the international law that talk about or govern this particular aspect. Technology is one thing that has rapidly developed over the years however it has failed to acknowledge the threat of cyber espionage which in very simple terms would mean cyber spying. This would include spying by one state over the sensitive information of another for any number of reasons. However, apart from a state’s intervention regarding the cyber espionage, there can also be many non-state actors that can be either used by states as a means to an end for their own good or these non-state actors can also act on their own accord to steal sensitive information from various powerful nation states for their own good.
CYBER ESPIONAGE AND INTERNATIONAL LAW
Many states including superpowers such as USA, Russia and China have agreed that cyberspace is inclusive of a state’s territory and thus international law would apply therein to impose responsibilities on nation states in this regard. However, the issue then arises with regards to the classification of cyber espionage and other cyber-crimes, considering the difference that they have when we compare them to traditional means of warfare in which most of the treaties, conventions or other legal instruments will apply. In this regard there are two very diverse ideas; one wherein independence of cyberspace is propagated and another wherein it is argued that no matter how large a cyberspace is, it will be located somewhere in the form or servers or even when we talk about cyber-crimes, they use some machinery, computer or any other technology which has physical components attached to it and thus it should come under the ambit of the nation states jurisdiction only and not be an independent system.
In this regard a further point of contention is the difference between cyber espionage and the traditional means of spying. Traditional means of spying naturally involved infringing a sovereign’s territory and then extracting relevant information from the sources available at hand. Therefore, as it is a direct violation of a state’s territory the same is a crime and covered under the international law. However, considering that cyber espionage does not directly result in any interference in a nation’s territory the same should not be regarded as a crime or even be compared to the traditional espionage methods. This would be a faulty assumption because as established previously cyberspace falls within the boundaries of a nation state itself and thus even if by extension it forms a part of its independent dominion where it can exercise a certain degree of control without any fear of outside interference or intrusion. Herein, the territorial integrity as well as the territorial sovereignty both of which are enshrined in the UN Charter would come into play, thus ensuring that any intervention or any intrusion in the cyberspace would also be an altercation with the internal affairs of the states and in very simple terms violation of its territorial integrity, thus in essence making it an offence and against the international law.
CONCLUSION AND THE WAY FORWARD
It is imperative to note that cyber espionage also often infringes upon the right to privacy of individuals in question and the same is also protected under various international instruments the most prominent being the Universal Declaration of Human Rights in this regard as well as national legislations. Considering that it has been established with the nation states themselves agreeing time and time again that cyber infrastructure is included in their territory and that cyber crimes are on a rise, it is the need of the hour that proper legal instruments are made to protect the sovereignty of the nation states when it comes to their cyber infrastructure. Herein, a proper balance has to be maintained between focusing on the damage that such cyber espionage can cause and how it is very different from physical espionage. Another aspect that has to be carefully looked into is whether this espionage is being done by another nation state or a non-state actor. In this regard extradition treaties especially including cyber-crimes in their domain would be of great help so that people who commit crimes from one country and infringe on the territorial sovereignty of another are not able to get away with the same.
















































































 onducted a total of five underground nuclear tests, breaking a 24-year self-imposed moratorium on nuclear testing. Pakistan followed, claiming 5 tests on May 28, 1998, and an additional test on May 30. The unannounced tests created a global storm of criticism, as well as a serious setback for decades of U.S. nuclear nonproliferation efforts in South Asia. On May 13, 1998, President Clinton imposed economic and military sanctions on India, mandated by Section 102 of the Arms Export Control Act (AECA), and applied the same sanctions to Pakistan on May 30. Some effects of the sanctions on India included: termination of $21 million in FY1998 economic development assistance; postponement of $1.7 billion in lending by the International Financial Institutions (IFI), as supported by the Group of Eight (G-8) leading industrial nations; prohibition on loans or credit from U.S. banks to the government of India; and termination of Foreign Military Sales under the Arms Export Control Act. Humanitarian assistance, food, or other agricultural commodities are excepted from sanctions under the law.
onducted a total of five underground nuclear tests, breaking a 24-year self-imposed moratorium on nuclear testing. Pakistan followed, claiming 5 tests on May 28, 1998, and an additional test on May 30. The unannounced tests created a global storm of criticism, as well as a serious setback for decades of U.S. nuclear nonproliferation efforts in South Asia. On May 13, 1998, President Clinton imposed economic and military sanctions on India, mandated by Section 102 of the Arms Export Control Act (AECA), and applied the same sanctions to Pakistan on May 30. Some effects of the sanctions on India included: termination of $21 million in FY1998 economic development assistance; postponement of $1.7 billion in lending by the International Financial Institutions (IFI), as supported by the Group of Eight (G-8) leading industrial nations; prohibition on loans or credit from U.S. banks to the government of India; and termination of Foreign Military Sales under the Arms Export Control Act. Humanitarian assistance, food, or other agricultural commodities are excepted from sanctions under the law. 
















 The first ministerial level meeting of QUAD was held on the sidelines of the United Nations General Assembly in New York. Before this, the QUAD had
The first ministerial level meeting of QUAD was held on the sidelines of the United Nations General Assembly in New York. Before this, the QUAD had AusIndEx is an exercise between India and Australia which was first held in 2015.The Australian
AusIndEx is an exercise between India and Australia which was first held in 2015.The Australian 







 On recommendations of the Japanese government, the four countries met at Manila, Philippines for ASEAN Regional Forum (ARF) originally, but also ended up having a meeting of what we call the first meeting of four nation states on issues of
On recommendations of the Japanese government, the four countries met at Manila, Philippines for ASEAN Regional Forum (ARF) originally, but also ended up having a meeting of what we call the first meeting of four nation states on issues of  On his official visit to India, Japanese PM Mr. Shinzo Abe reinforced the ties of two nations, i.e., Japan and India with his famous speech about
On his official visit to India, Japanese PM Mr. Shinzo Abe reinforced the ties of two nations, i.e., Japan and India with his famous speech about  In 2007, Japanese President Shinzo Abe resigned from his post citing health reasons. This had a significant impact on QUAD as he was the architect & advocate of QUAD. His successor, Yasuo Fukuda, did not take up QUAD with such zeal leading to dormancy of the forum. (
In 2007, Japanese President Shinzo Abe resigned from his post citing health reasons. This had a significant impact on QUAD as he was the architect & advocate of QUAD. His successor, Yasuo Fukuda, did not take up QUAD with such zeal leading to dormancy of the forum. (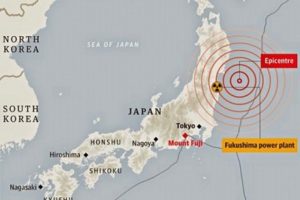 Japan earthquake and tsunami of 2011, also called Great Sendai Earthquake or Great Tōhoku Earthquake, was a 9.0 magnitude earthquake which struck below the floor of the Western Pacific at 2:49 PM. The powerful earthquake affected the northeastern coast of Honshu, Japan’s main island, and also initiated a series of large tsunami waves that devastated coastal areas of Japan, which also led to a major nuclear accident. Japan received aid from India, US, Australia as well as other countries. US Navy aircraft carrier was dispatched to the area and Australia sent search-and-rescue teams.
Japan earthquake and tsunami of 2011, also called Great Sendai Earthquake or Great Tōhoku Earthquake, was a 9.0 magnitude earthquake which struck below the floor of the Western Pacific at 2:49 PM. The powerful earthquake affected the northeastern coast of Honshu, Japan’s main island, and also initiated a series of large tsunami waves that devastated coastal areas of Japan, which also led to a major nuclear accident. Japan received aid from India, US, Australia as well as other countries. US Navy aircraft carrier was dispatched to the area and Australia sent search-and-rescue teams.  India and Australia signed the
India and Australia signed the  The India-Japan Agreement for Cooperation in the Peaceful Uses of Nuclear Energy was signed on 11 November, 2016 and came into force on 20 July, 2017 which was representative of strengthening ties between India and Japan. Diplomatic notes were exchanged between Dr. S. Jaishankar and H.E. Mr. Kenji Hiramatsu, Ambassador of Japan to India. (
The India-Japan Agreement for Cooperation in the Peaceful Uses of Nuclear Energy was signed on 11 November, 2016 and came into force on 20 July, 2017 which was representative of strengthening ties between India and Japan. Diplomatic notes were exchanged between Dr. S. Jaishankar and H.E. Mr. Kenji Hiramatsu, Ambassador of Japan to India. ( The foreign ministry
The foreign ministry The Officials of QUAD member countries met in Singapore on November 15, 2018 for consultation on regional & global issues of common interest. The main discussion revolved around connectivity, sustainable development, counter-terrorism, maritime and cyber security, with the view to promote peace, stability and prosperity in the
The Officials of QUAD member countries met in Singapore on November 15, 2018 for consultation on regional & global issues of common interest. The main discussion revolved around connectivity, sustainable development, counter-terrorism, maritime and cyber security, with the view to promote peace, stability and prosperity in the  The 23rd edition of trilateral Malabar maritime exercise between India, US and Japan took place on 26 September- 04 October, 2019 off the coast of Japan.
The 23rd edition of trilateral Malabar maritime exercise between India, US and Japan took place on 26 September- 04 October, 2019 off the coast of Japan.  After the first ministerial level meeting of QUAD in September, 2019, the senior officials of US, Japan, India and Australia again met for consultations in Bangkok on the margins of the East Asia Summit. Statements were issued separately by the four countries. Indian Ministry of External Affairs said “In statements issued separately by the four countries, MEA said, “proceeding from the strategic guidance of their Ministers, who met in New York City on the sidelines of the UN General Assembly recently, the officials exchanged views on ongoing and additional practical cooperation in the areas of connectivity and infrastructure development, and security matters, including counterterrorism, cyber and maritime security, with a view to promoting peace, security, stability, prosperity in the Indo-Pacific region.”
After the first ministerial level meeting of QUAD in September, 2019, the senior officials of US, Japan, India and Australia again met for consultations in Bangkok on the margins of the East Asia Summit. Statements were issued separately by the four countries. Indian Ministry of External Affairs said “In statements issued separately by the four countries, MEA said, “proceeding from the strategic guidance of their Ministers, who met in New York City on the sidelines of the UN General Assembly recently, the officials exchanged views on ongoing and additional practical cooperation in the areas of connectivity and infrastructure development, and security matters, including counterterrorism, cyber and maritime security, with a view to promoting peace, security, stability, prosperity in the Indo-Pacific region.” US 2+2 Ministerial Dialogue was held on 18 December, 2019, in Washington DC. Secretary of State Michael R. Pompeo and Secretary of Defense Mark T. Esper will host Indian Minister of External Affairs Dr. S. Jaishankar and Minister of Defense Shri Rajnath Singh. The discussion focussed on deepening bilateral strategic and defense cooperation, exchanging perspectives on global developments, and our shared leadership in the Indo-Pacific region.The two democracies signed the Industrial Security Annex before the 2+2 Dialogue. Assessments of the situation in Afghanistan, Pakistan, Nepal, Sri Lanka, and the Indian Ocean region in general were shared between both countries. (
US 2+2 Ministerial Dialogue was held on 18 December, 2019, in Washington DC. Secretary of State Michael R. Pompeo and Secretary of Defense Mark T. Esper will host Indian Minister of External Affairs Dr. S. Jaishankar and Minister of Defense Shri Rajnath Singh. The discussion focussed on deepening bilateral strategic and defense cooperation, exchanging perspectives on global developments, and our shared leadership in the Indo-Pacific region.The two democracies signed the Industrial Security Annex before the 2+2 Dialogue. Assessments of the situation in Afghanistan, Pakistan, Nepal, Sri Lanka, and the Indian Ocean region in general were shared between both countries. ( The foreign ministers of QUAD continued their discussions from the last ministerial level meeting in 2019, on 6 October, 2020. While there was no joint statement released, all countries issued individual readouts. As per the issue readout by India, the discussion called for a coordinated response to the challenges including financial problems emanating from the pandemic, best practices to combat Covid-19, increasing the resilience of supply chains, and enhancing access to affordable vaccines, medicines and medical equipment. There was also a focus on maintaining stability in the Indo-Pacific region amidst growing tensions. Australian media release mentions “We emphasised that, especially during a pandemic, it was vital that states work to ease tensions and avoid exacerbating long-standing disputes, work to counter disinformation, and refrain from malicious cyberspace activity. Ministers reiterated that states cannot assert maritime claims that are inconsistent with international law, particularly the United Nations Convention on the Law of the Sea (UNCLOS).”
The foreign ministers of QUAD continued their discussions from the last ministerial level meeting in 2019, on 6 October, 2020. While there was no joint statement released, all countries issued individual readouts. As per the issue readout by India, the discussion called for a coordinated response to the challenges including financial problems emanating from the pandemic, best practices to combat Covid-19, increasing the resilience of supply chains, and enhancing access to affordable vaccines, medicines and medical equipment. There was also a focus on maintaining stability in the Indo-Pacific region amidst growing tensions. Australian media release mentions “We emphasised that, especially during a pandemic, it was vital that states work to ease tensions and avoid exacerbating long-standing disputes, work to counter disinformation, and refrain from malicious cyberspace activity. Ministers reiterated that states cannot assert maritime claims that are inconsistent with international law, particularly the United Nations Convention on the Law of the Sea (UNCLOS).” On September 24, President Biden hosted Prime Minister Scott Morrison of Australia, Prime Minister Narendra Modi of India, and Prime Minister Yoshihide Suga of Japan at the White House for the first-ever in-person Leaders’ Summit of the QUAD. The leaders released a Joint Statement which summarised their dialogue and future course of action. The regional security of the Indo-Pacific and strong confidence in the ASEAN remained on the focus along with response to the Pandemic.
On September 24, President Biden hosted Prime Minister Scott Morrison of Australia, Prime Minister Narendra Modi of India, and Prime Minister Yoshihide Suga of Japan at the White House for the first-ever in-person Leaders’ Summit of the QUAD. The leaders released a Joint Statement which summarised their dialogue and future course of action. The regional security of the Indo-Pacific and strong confidence in the ASEAN remained on the focus along with response to the Pandemic.  The QUAD Vaccine Partnership was announced at the first QUAD Summit on 12 March 2021 where QUAD countries agreed to deliver 1.2 billion vaccine doses globally. The aim was to expand and finance vaccine manufacturing and equipping the Indo-Pacific to build resilience against Covid-19. The launch of a senior-level QUAD Vaccine Experts Group, comprised of top scientists and officials from all QUAD member governments was also spearheaded.
The QUAD Vaccine Partnership was announced at the first QUAD Summit on 12 March 2021 where QUAD countries agreed to deliver 1.2 billion vaccine doses globally. The aim was to expand and finance vaccine manufacturing and equipping the Indo-Pacific to build resilience against Covid-19. The launch of a senior-level QUAD Vaccine Experts Group, comprised of top scientists and officials from all QUAD member governments was also spearheaded.  Although the Tsunami Core group had to be disbanded on fulfilment of its purpose, however the quadrilateral template that formed remained intact as a successful scaffolding of four countries, as stated by authors Patrick Gerard Buchan and Benjamin Rimland in their diplomatic brief about QUAD ( you can access the brief at
Although the Tsunami Core group had to be disbanded on fulfilment of its purpose, however the quadrilateral template that formed remained intact as a successful scaffolding of four countries, as stated by authors Patrick Gerard Buchan and Benjamin Rimland in their diplomatic brief about QUAD ( you can access the brief at  Secretary of State Colin Powell stated that the Core Tsunami Group was to be disbanded and folded and clubbed with the broader United Nations led Relief Operations. In a Tsunami Relief Conference in Jakarta, Secretary Powell stated that
Secretary of State Colin Powell stated that the Core Tsunami Group was to be disbanded and folded and clubbed with the broader United Nations led Relief Operations. In a Tsunami Relief Conference in Jakarta, Secretary Powell stated that  Soon after the Earthquake and Tsunami crisis, humanitarian reliefs by countries, viz., US, India, Japan, and Australia started to help the 13 havoc-stricken countries. The US initially promised $ 35 Millions in aid. However, on 29
Soon after the Earthquake and Tsunami crisis, humanitarian reliefs by countries, viz., US, India, Japan, and Australia started to help the 13 havoc-stricken countries. The US initially promised $ 35 Millions in aid. However, on 29 At 7:59AM local time, an earthquake of 9.1 magnitude (undersea) hit the coast of Sumatra, an Indonesian island. As a result of the same, massive waves of Tsunami triggered by the earthquake wreaked havoc for 7 hours across the Indian Ocean and to the coastal areas as far away as East Africa. The infamous Tsunami killed around 225,000 people, with people reporting the height of waves to be as high as 9 metres, i.e., 30 feet. Indonesia, Srilanka, India, Maldives, Thailand sustained horrendously massive damage, with the death toll exceeding 200,000 in Northern Sumatra’s Ache province alone. A great many people, i.e., around tens of thousands were found dead or missing in Srilanka and India, mostly from Andaman and Nicobar Islands of Indian territory. Maldives, being a low-lying country, also reported casualties in hundreds and more, with several non-Asian tourists reported dead or missing who were vacationing. Lack of food, water, medicines burgeoned the numbers of casualties, with the relief workers finding it difficult to reach the remotest areas where roads were destroyed or civil war raged. Long-term environmental damage ensued too, as both natural and man-made resources got demolished and diminished.
At 7:59AM local time, an earthquake of 9.1 magnitude (undersea) hit the coast of Sumatra, an Indonesian island. As a result of the same, massive waves of Tsunami triggered by the earthquake wreaked havoc for 7 hours across the Indian Ocean and to the coastal areas as far away as East Africa. The infamous Tsunami killed around 225,000 people, with people reporting the height of waves to be as high as 9 metres, i.e., 30 feet. Indonesia, Srilanka, India, Maldives, Thailand sustained horrendously massive damage, with the death toll exceeding 200,000 in Northern Sumatra’s Ache province alone. A great many people, i.e., around tens of thousands were found dead or missing in Srilanka and India, mostly from Andaman and Nicobar Islands of Indian territory. Maldives, being a low-lying country, also reported casualties in hundreds and more, with several non-Asian tourists reported dead or missing who were vacationing. Lack of food, water, medicines burgeoned the numbers of casualties, with the relief workers finding it difficult to reach the remotest areas where roads were destroyed or civil war raged. Long-term environmental damage ensued too, as both natural and man-made resources got demolished and diminished.
No responses yet